What is Nikto?
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
How does it work?
Nikto is by no means a stealthy tool. It will make over 2000 HTTP GET requests to the web server, creating a large number of entries in the web servers log files. This noise is actually an excellent way to test an in place Intrusion Detection System (IDS) that is in place. Any web server log monitoring, host based intrusion detection (HIDS) or network based intrusion detection (NIDS) should detect a Nikto scan.
Experiment
for this experiment, the website that I am going to use will be scdc.binus.ac.id.
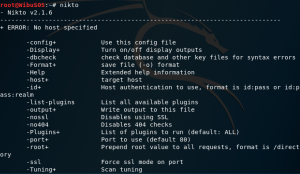
you can get detailed explanation by typing “nikto” on your terminal.
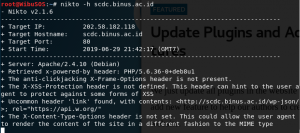
To use Nikto, it’s really straightforward. If your website is secure (using ssl), you just simply add -ssl after typing in domain name (nikto -h DOMAIN -ssl). If it’s not, simply just omit -ssl part.
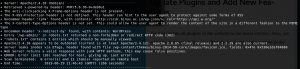
After scanning done, you can get any vulnerabilities or misconfigurations found from external perspective. But remember, using Nikto means you are also exposing yourself to victim’s sysadmin. From image above, you can see that there are some informations there, like outdated Apache server, PHP version, WordPress CMS, etc.
