This is my second project which demonstrates MiTM attack using a tool called Burp Suite. It utilizes a forged SSL to eavesdrop victim’s requested contents.
The outline of this project basically is intercepting victim’s browser through our forged SSL. Our SSL become the so-called “Middle-man” which any requested contents will go through our SSL first. The requested contents then can be seen using Burp Suite
Steps:
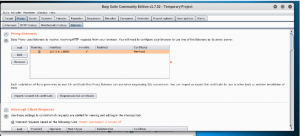
Open Burp Suite -> Proxy -> Options
Tick the running checkbox to activate the proxy
Click edit
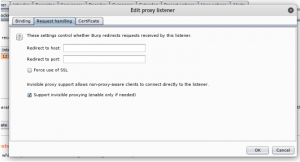
Got to Request handling
Tick Support invisible proxying
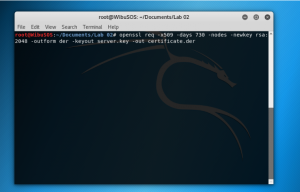
Open terminal
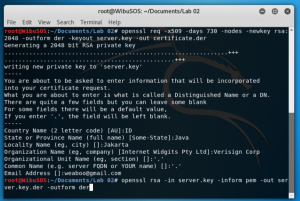
Type “openssl req -x509 -days 730 -nodes -newkey rsa:2048 -outform der -keyout server.key -out certificate.der” to create the certificate
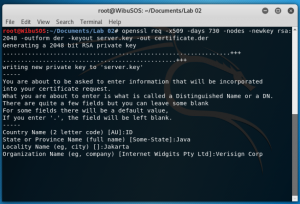
Fill in the information required and use “Verisign Corp” in the Organization name field
Type “openssl rsa -in server.key -inform pem -out server.key.der -outform der” to write the RSA key
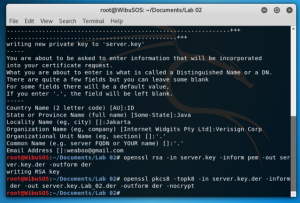
Type “openssl pkcs8 -topk8 -in server.key.der -inform der -out server.key.pkcs8.der -outform der -nocrypt” to get the key used for decryption
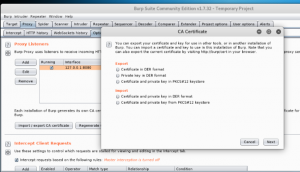
Back to Burp Suite, click “Import / export CA certificate” and choose “Certificate and private key in DER format” in Import
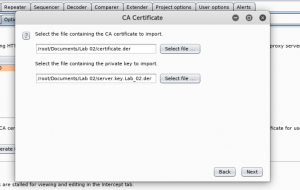
Select “certificate.der” and “server.key.Lab_02.der”
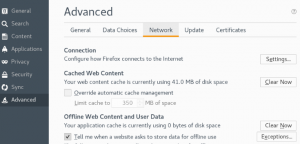
Open firefox -> Preferences -> Advanced -> Network -> Click Settings
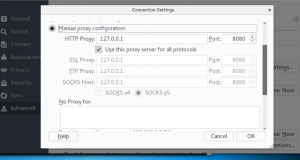
Choose “Manual proxy configuration”
Type “127.0.0.1” in the HTTP Proxy and “8080” in the Port
Tick “Use this proxy server for all protocols”
Erase all the things inside the “No Proxy for” field -> click OK
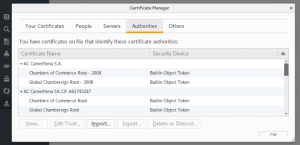
Open certificates tab -> click “View certificates”
Click Import
Choose file named “certificate.der”
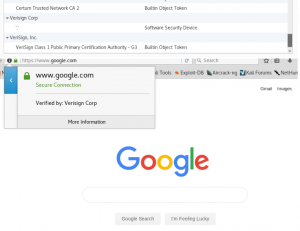
To see the complete tutorial with images, you can see through this link:
https://drive.google.com/open?id=10Tc5JH83xfpCrGZbcuFdHOdBfFRckvz5
