Synopsis
On this blog post, I am going to experiment with Arpspoofing (without using Ettercap). The target of this experiment is to get credentials that can be exposed via TCPdump.
Preparation
For this experiment to work, you need to prepare:
– 2 VMs, bridged to the same network
Experiment
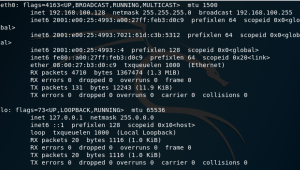
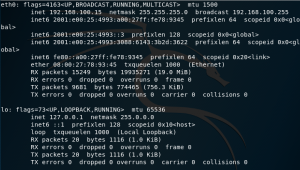
For starters, you have to get the IP address of both VMs. You can get it by typing “ifconfig”.
![]()
Next, check the gateway for both VMs. Gateway must be the same.
![]()
Set your attacker VM to ip forward for every incoming traffic. If not, your victim won’t get any traffic later.
![]()
![]()
after ip forwarding, now you just need to activate arpspoof by typing “arpspoof -t TARGET HOST”. Basically, you have to do it twice. First, you have to spoof the victim into thinking you are the gateway. you can do it by putting VICTIM IP to TARGET and GATEWAY IP to HOST. Second, you also have to spoof the gateway itself, make it thinking you are the victim here. Simply do it by typing the command above again but changing TARGET to GATEWAY IP and HOST to VICTIM IP.
![]()
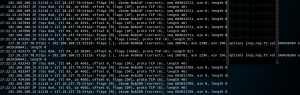
After doing arpspoof command above, you should be getting packets now (if you open browser and browse something on victim). Now, you just need to filter it. Using TCPdump command “tcpdump host TARGET IP and not arp -vv”, you can filter incoming packets from victim.
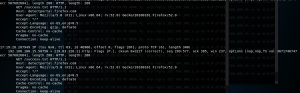
I tried to open twitter on victim. As you can see, there is a header info there and the rest is just normal packets. When I tried to log in, it failed to get the credential due to it being hashed.
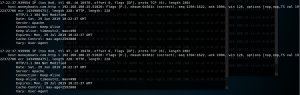
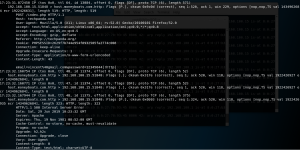
Last is techpanda. This time when i tried to use random credential to log in, it actually managed to capture it successfully as you can see from 2nd image.
