What is Nmap?
Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.
How does it work?
Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
Experiment
for this experiment, the website that I am going to use will be team3.pentest.id.
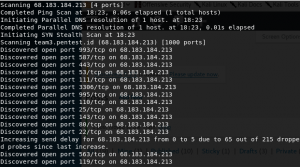
I used one of the basic command, nmap -v TARGET IP to look for all open ports on the target. -v stands for verbose. But, the informations regarding the ports aren’t detailed.
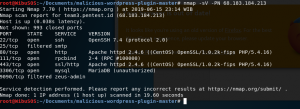
Now we scan the target again using nmap -sV -PN TARGET IP. -sV will probe service / version info on every port. -PN is used to skip host discovery, thus resulting in faster scan. Now you can see more detailed information such as service and its version on every port.
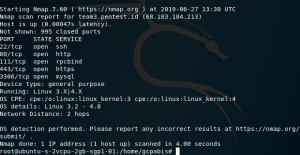
you can also use -O (nmap -O TARGET IP for example) to detect specifically what OS is running one the target. based on the result above, the target ran Linux 3.2 – 4.8.
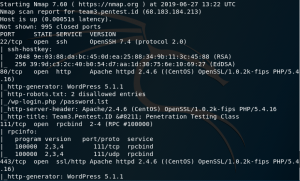
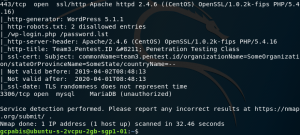
To get more information, I once again used nmap -A -PN TARGET IP. -A will make your scan targeting OS and version detection + traceroute and scripts. As you can see from the result, you can see what service is associated with every port like 22 for ssh for example. there is also state, which is open, and the version information. Below, you can see another information like the hostkey.
