In this experiment, we are going back to Social-Engineering. It’s basically the same as previous post which also made use of website forgery to get credential. But, this time we are going to simulate it in 2 VMs.
Before going deeper, we must first understand about Social-Engineering using SEToolkit, Arpspoof, and Dnsspoof. For SET, you can go to previous post.
What is Arpspoof?
ARP stands for Address Resolution Protocol and it allows the network to translate IP addresses into MAC addresses. Arpspoof constantly sends the victim computer ARP answers telling him that the MAC address belonging to the IP of the gateway machine (router) is our MAC address. After some time the victim computer will believe us and makes a wrong entry in his ARP cache. Next time the victim wants to send an IP packet to the gateway he sends the ethernet frame to our MAC address so actually we get the IP packet. We do the same thing with the gateway machine just the other way round.
What is Dnsspoof?
Dnsspoof works similarly to Arpspoof. It lets you forge DNS responses for a DNS server on the local network . DNS runs on User Datagram Protocol (UDP), a connectionless protocol, a DNS client will send out a query and expect a response . The query is assigned a pseudo random identification number which should be present in the answer from the DNS server. Then when the answer from the DNS server will be received , it will just have to compare both numbers if they’re the same, the answer is taken as valid, otherwise it will be simply ignored . The DNS protocol relies on UDP for requests (TCP is used only for zone transfers –> communications between DNS servers), which means that it is easy to send a packet coming from a fake IP since there are no SYN/ACK numbers (Unlike TCP, UDP doesn’t provide a minimum of protection against IP spoofing).
Experiment
For starters, we need to prepare 2 VMs and connect it via bridge or same network and the website we are going to use is https://www.techpanda.org/
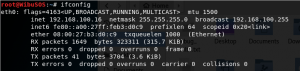
Check both of the IP address and also the gateway address (you can check the gateway by typing “route -n”).
![]()
Open SEToolkit.
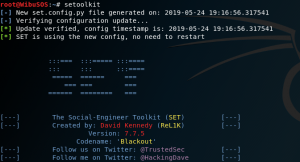
Choose 1.
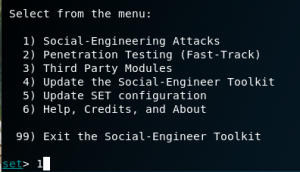
Choose 2.
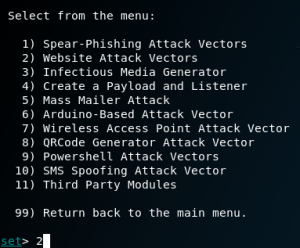
Choose 3.
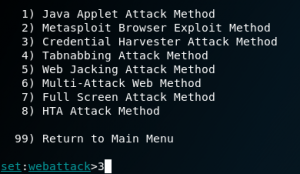
Choose 2.
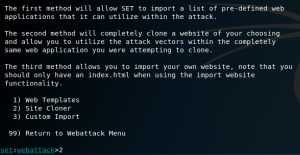
Type attacker’s IP address and URL of the website that you want to clone.
![]()
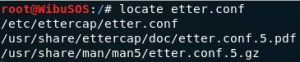
Now after website cloning is done, we work on the spoofing. locate “etter.conf” and open it using leafpad or any text editor you prefer.
![]()
Go to “iptables” section and delete the “#” symbol to activate it.


Locate “etter.dns” and edit it using text editor. Etter.dns basically contains mapping of URL and its respective IP address. It will be used to build a local DNS server.
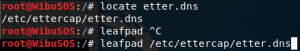
Go to section Microsoft. Change every URL into your website’s URL and the IP address into the attacker’s.

Open Ettercap.

Start unified sniffing.
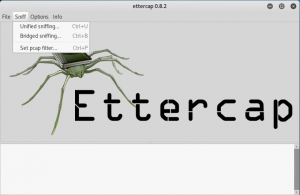
If you use eth0 for network interface between 2 VMs, choose it.
Stop the sniffing.
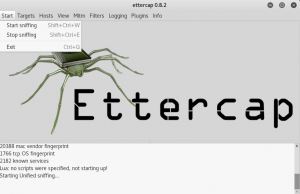
Scan for any available hosts and list it.
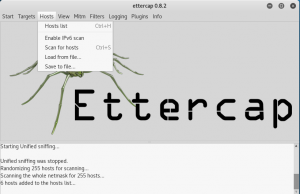
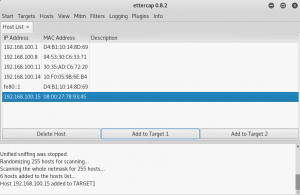
Find the victim’s IP address and the gateway address and put it into target 1 and target 2 respectively.
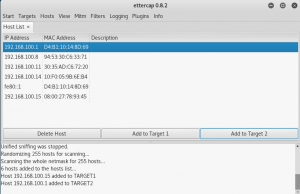
Choose Mitm > ARP poisoning and tick “Sniff remote connection”.
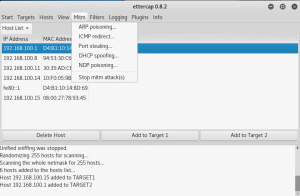
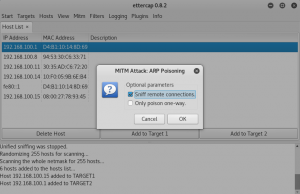
Choose Plugins > Manage the plugins > find dns_spoof.
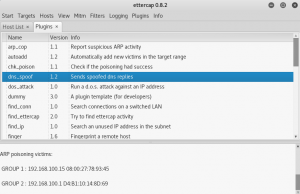
After finishing those steps above, start the unified sniffing again.
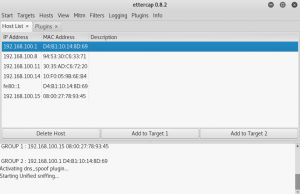
Now, the spoofing is done and the victim should regard you as the gateway and also the local DNS server.
To prove it, type https://www.techpanda.org/ onto the victim’s URL bar.
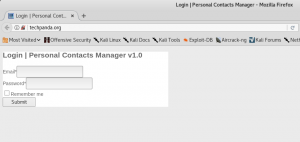
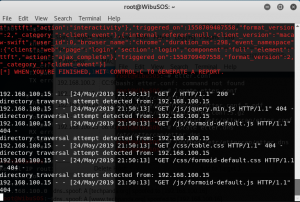
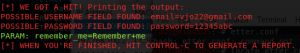
As you can see the connection is not secure. It proves that the website has been forged and it’s not the real one (the real one uses secure connection). To prove it further, insert your credential and submit it.
Now back to attacker’s terminal, you can see the credential there.