What is SEToolkit?
The Social-Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. Its main purpose is to augment and simulate social-engineering attacks and allow the tester to effectively test how a targeted attack may succeed.
How does it work?
SET makes use of Social-Engineering as its core function. Social-Engineering is an attack vector that relies heavily on human interaction and often involves manipulating people into breaking normal security procedures and best practices in order to gain access to systems, networks or physical locations, or for financial gain.
Social engineers use a wide variety of tactics to perform attacks. The first step in most social engineering attacks is for the attacker to perform research and reconnaissance on the target. From there, the hacker can design an attack based on the information collected and exploit the weakness uncovered during the reconnaissance phase. If the attack is successful, hackers have access to sensitive data — such as credit card or banking information — have made money off the targets or have gained access to protected systems or networks.
Experiment
for this experiment, I am going to try phishing method by using website cloner function in SEToolkit. The website that I am going to clone is https://twitter.com/login
For this experiment, we only are going to use 1 VM. this VM acts both as the attacker and the victim. First, open terminal and type setoolkit.
![]()
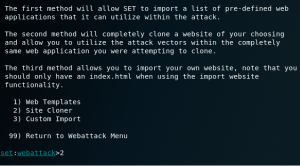
From there, you will be taken to main menu. As you can see, there are a number of functions here that can be used. Choose 1 for Social-Engineering attacks.
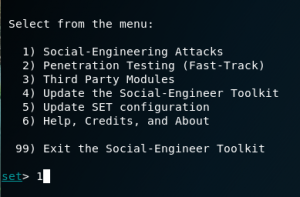
Choose 2 for website attack vectors because we are going to make use of website forgery for phishing.
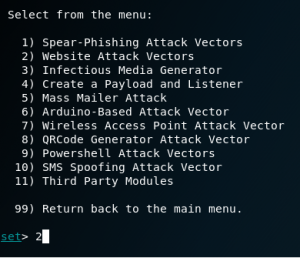
Choose 3 for credential harvester attack method.
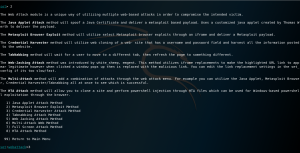
Choose 2 to use site cloner.
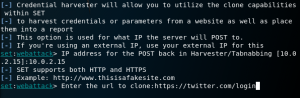
In this step, you are needed to enter the attacker’s IP address. This IP address will be used to host the forged website.
Next, you are required to enter the URL of the website that you want to clone, in this case: https://twitter.com/login
Now open your browser (VM’s browser) and type the attacker’s IP address. You will then see this:
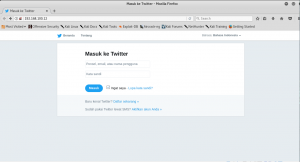
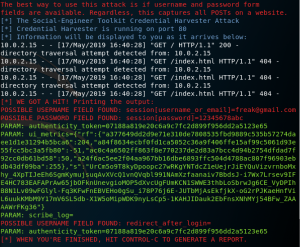
The website has been successfully forged (can be seen from attacker’s IP address in the URL bar). Now you type your credential there (can be a fake one) and press “Masuk”.
As you can see from the image below, SEToolkit acquired the inputted credential from the forged twitter website and displayed it on the terminal.