In 1st week, I learned the surface of ethical hacking. Before you dive into the world of hacking, we must first learn the common terms used in ethical hacking, such as hackers, crackers, and ethical hacker. packet monkeys, tiger box, blue team, red team, and so on.
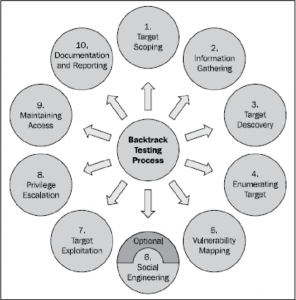
I also learned the methodologies used in pentest which are white box, black box, and gray box model. There is also other methodology which involves backtrack testing process. it is spanned into 10 steps of process from the start and finish.
Not only those, I also learned some of the certifications which are related to the world of ethical hacking. With great power, comes great responsibility. If you have the power of ethical hacking, you must first learn all the laws involved in it because not every nation allows you to do pentest without authorization.
