In this week, the tool that i want to experiment is Maltego. for the experiment subject, i am going to use team3.pentest.id and Facebook.com. But, before we start experimenting, let’s first learn what Maltego is.
Maltego is a forensic tool that can be used to gather information about either a network or an individual. informations gathered can be subdomains, IP address range, WHOIS info, all of the email addresses, and relationship between the target domain and other.
For start, you must first create your account on Maltego CE website before using Maltego. You can go through this link: https://www.paterva.com/web7/buy/maltego-clients/maltego-ce.php
After that, you can initiate information finding by going to tab machines and pick which machines you want to use. Machines are basically a choice of method you want to use to get your info. Different machine gives you different result. for example, company stalker machine gives you any available email address from the domain. In this case, I use footprint L3 because it’s the most comprehensive machine and gives information like the subdomains, the IP address range, the WHOIS info, all of the email addresses, and the relationship between the target domain and others.
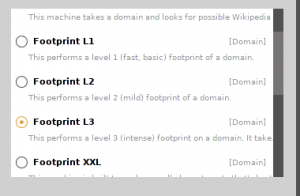
After choosing your machine, you input the domain. in this case pentest3.team.id
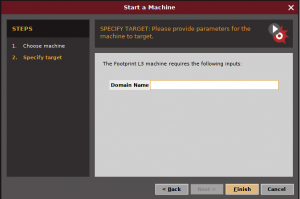
Unfortunately, when I tried to use maltego on pentest3.team.id, it din’t give any result.
This image below is the result of using Maltego on Facebook.com

As you can see from this result, this is the only info that could be gotten from facebook. it shows you what technologies that build up Facebook.
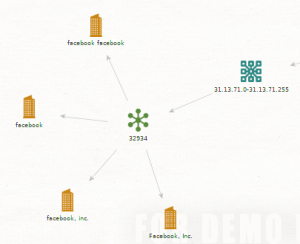
this relationship also shows you what companies that connect to the website and its netblocks used.
Now continuing from team3.pentest.id, you can also do finding from palette tab below:

As you can see, you can drag these tools from palette into your workspace. for example, I am gonna use IP address from team3.pentest.id.

and starting from this, you can do all sort of transform just like below:

From there, I am gonna use all transform to find every available lead.


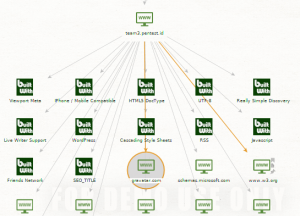
Those pictures above are the results from transform. You can see that the IP address leads to digital ocean and the DNS name leads to the technologies used by the website.
