This time I am gonna experiment with WPScan to find vulnerabilities on WordPress blog. Not just vulnerabilities, you can also get if there is any weak passwords or security issue present on your WordPress blog. All these check is based on the database which is maintained by WPScan team.
For this experiment, I am gonna use website pentest3.team.id
First, you open terminal and type “wpscan” to open it.
From there, there will be a header appears on the terminal. After that you type in format “wpscan –url [this is your url target]”
![]()
this command scan every exposed vulnerability on your target’s website such as, themes, plugins, wordpress ver., backend used and its ver., server used, etc.
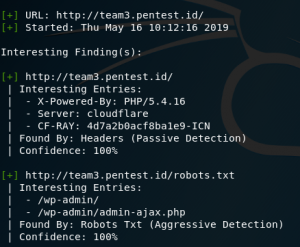
As you can see, it finds informations like what the server is, PHP with its ver. as backend. It also finds txt file called “robots” which contains informations about subdomains (“/wp-admin/” and “/wp-admin/admin-ajax.php”).
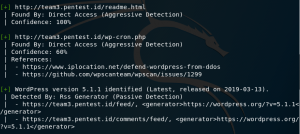
it also finds other subdomains such as “readme.html” and “wp-cron.php”. you also see what ver. of WordPress is currently used.
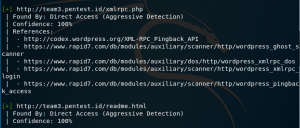
It also finds other kind of vulnerabilities like “xmlrpc.php” for example.

Not jus those above, it also detects the theme used in your WordPress and its ver. as you can exploit the website based on the exposed vulnerabilities that go along with its theme ver.
It also has specific commands such as “wpscan –url [this is your url target] –enumerate u” which is used to find any registered usernames in your WordPress site.
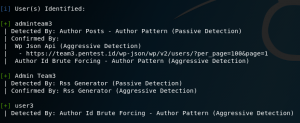
As you can see from the result, the website has currently 3 registered usernames.
There are also another commands “wpscan –url [this is your url target] –enumerate vp” and “wpscan –url [this is your url target] –enumerate vt”. vp is used to find vulnerabilities related to plugins used and vt is used to find it on theme used.