What is TheHarvester?
TheHarvester is a program which is used to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
What is it for?
This tool is intended to help Penetration testers in the early stages of the penetration test in order to understand the customer footprint on the Internet. It is also useful for anyone that wants to know what an attacker can see about their organization.
Experiment
for this experiement, the website that I am going to use will be team3.pentest.id.
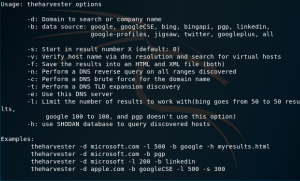
As you can see above, there are a lot of command you can use there.
The most common one will be -d, -l, and -b. -d is used to describe the domain or company name. -l is used to limit the number of results for harvesting, and -b is used to describe which data sources you are going to use.

in this example, I used googleCSE as the data source. Unfortunately, it didn’t find results.

you can also use command “all” to find results from every listed data source.

Unfortunately, after finding from all data sources, it still found no results.
Next, I tried to find information regarding scdc.binus.ac.id.

I limited the result to 50 and get every information available on every data source.
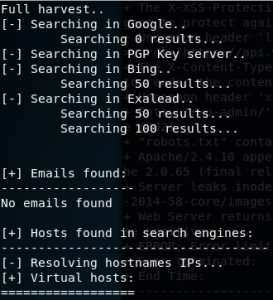
Once again, I can’t find any lead regarding scdc.binus.ac.id.
