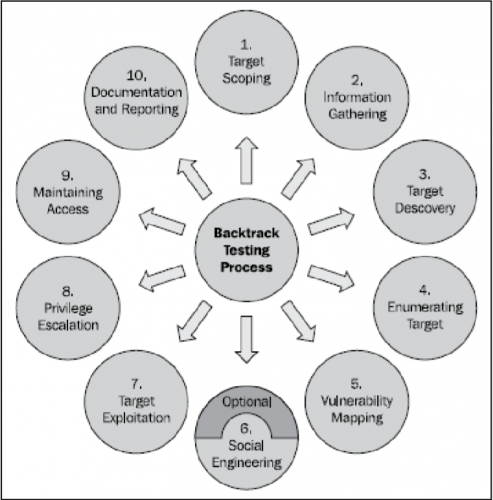
Surface of Ethical Hacking
In 1st week, I learned the surface of ethical hacking. Before you dive into the world of hacking, we must first learn the common terms used in ethical hacking, such […]


In 1st week, I learned the surface of ethical hacking. Before you dive into the world of hacking, we must first learn the common terms used in ethical hacking, such […]
In this project, we are required to do a penetration testing on a designated website My team: Vincent Joyan Ryan Anggada Kho 03-05-2019 We created our project planning for our […]
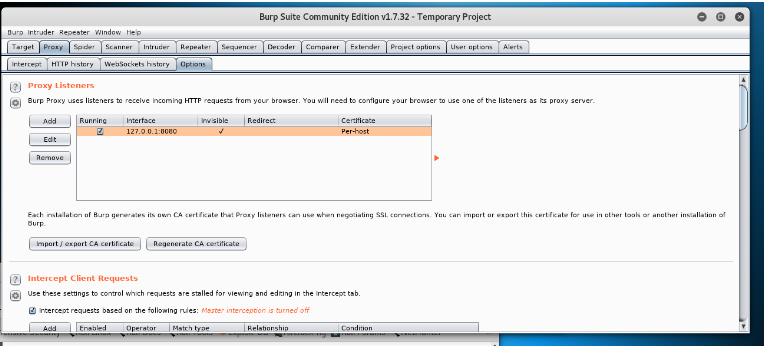
This is my second project which demonstrates MiTM attack using a tool called Burp Suite. It utilizes a forged SSL to eavesdrop victim’s requested contents. The outline of this project […]
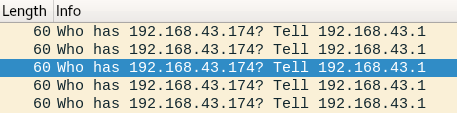
This is my first project which demonstrates how to do eavesdropping attack using tcpdump method. tcpdump is a command line network sniffer, used to capture network packets. When you have […]