Getting Credential using SEToolkit, Arpspoof and Dnsspoof
In this experiment, we are going back to Social-Engineering. It’s basically the same as previous post which also made use of website forgery to get credential. But, this time we […]


In this experiment, we are going back to Social-Engineering. It’s basically the same as previous post which also made use of website forgery to get credential. But, this time we […]
In this experiment, we are going to exploit Bash Shellshock vulnerability using Metasploit. But first, let’s get to know what Shellshock is. What is Shellshock? Shellshock, also known as Bashdoor, […]
What is SEToolkit? The Social-Engineer Toolkit (SET) was created and written by the founder of TrustedSec. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. Its main purpose […]
What is Metagoofil? Metagoofil is an information gathering tool designed for extracting metadata of public documents (pdf,doc,xls,ppt,docx,pptx,xlsx) belonging to a target company. How does it work? Metagoofil will perform a […]
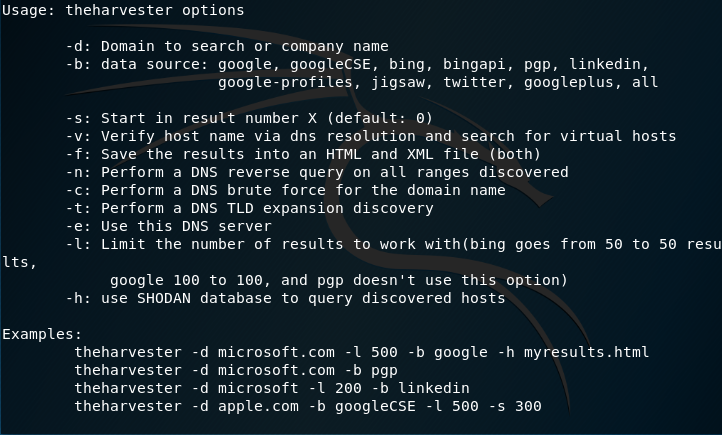
What is TheHarvester? TheHarvester is a program which is used to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key […]
This time I am gonna experiment with WPScan to find vulnerabilities on WordPress blog. Not just vulnerabilities, you can also get if there is any weak passwords or security issue […]
In this week, the tool that i want to experiment is Maltego. for the experiment subject, i am going to use team3.pentest.id and Facebook.com. But, before we start experimenting, let’s […]
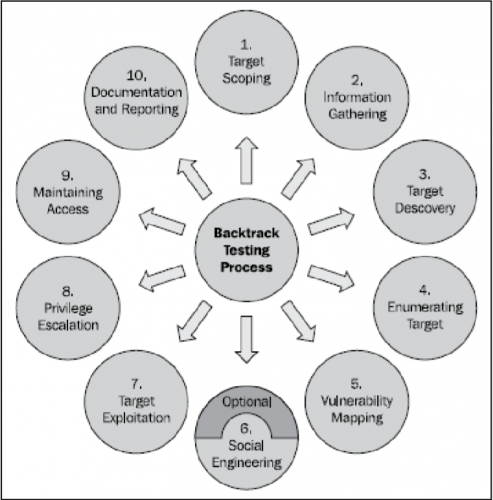
In 1st week, I learned the surface of ethical hacking. Before you dive into the world of hacking, we must first learn the common terms used in ethical hacking, such […]
In this project, we are required to do a penetration testing on a designated website My team: Vincent Joyan Ryan Anggada Kho 03-05-2019 We created our project planning for our […]
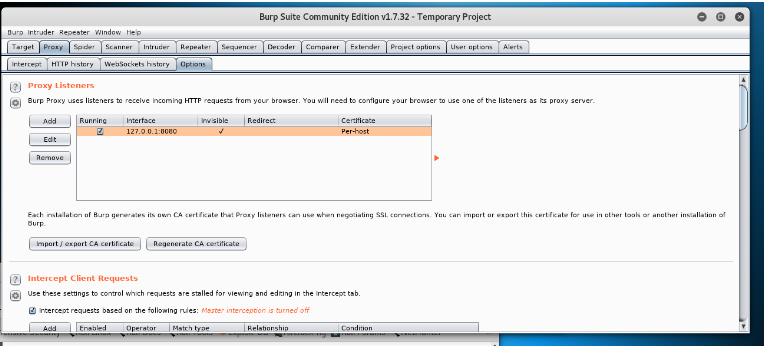
This is my second project which demonstrates MiTM attack using a tool called Burp Suite. It utilizes a forged SSL to eavesdrop victim’s requested contents. The outline of this project […]